1. Introduction
TRIPLE is a secure messaging protocol engineered for tomorrow's threats â€" and today's vulnerabilities. Unlike traditional math-based encryption, TRIPLE uses pointer-array logic, polymorphic transformation, and volatile memory to create randomized, session-specific languages. It's restartable, zero-trust by design, and resilient to both quantum computing and AI interception. When standard encryption breaks, TRIPLE keeps your data incomprehensible.
TRIPLE (Time Randomizing Interface Protocol Language Encryption) is a quantum-resistant encryption protocol that evolves a dynamic, shared language between communicating systems. It avoids fixed keys, replacing them with pointer-based randomized encoding arrays reset by time or traffic volume.
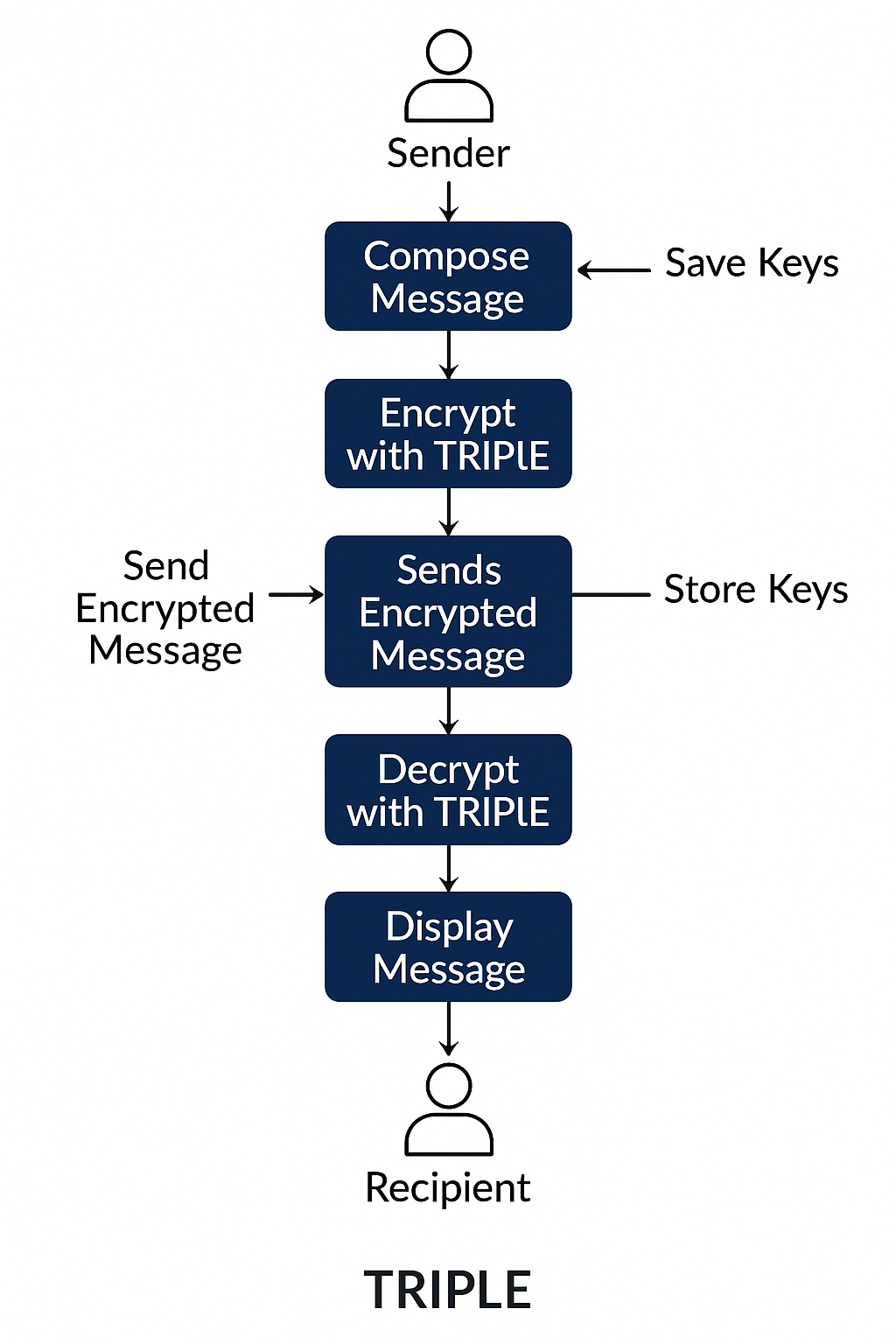
2. TRIPLE System Flow Diagrams
TRIPLE's functionality is illustrated in four key areas: Key Creation, Protocol Overview, Pointer Array Encryption, and Sender/Receiver Exchange. These show how sessions start, encrypt, reset, and resume.
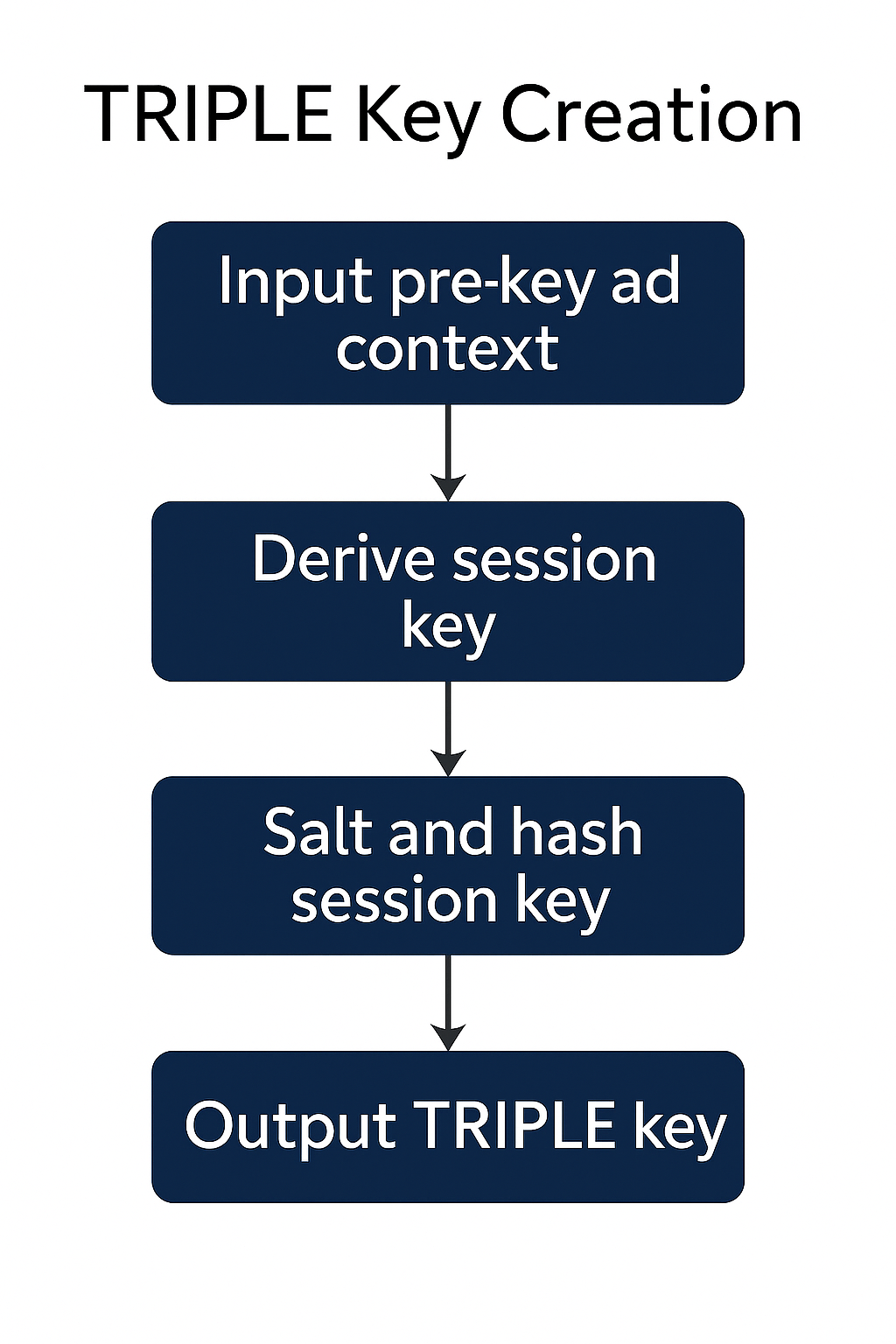
Key Creation Process
Dynamic generation of session-specific encoding arrays based on shared seed data and pointer logic.
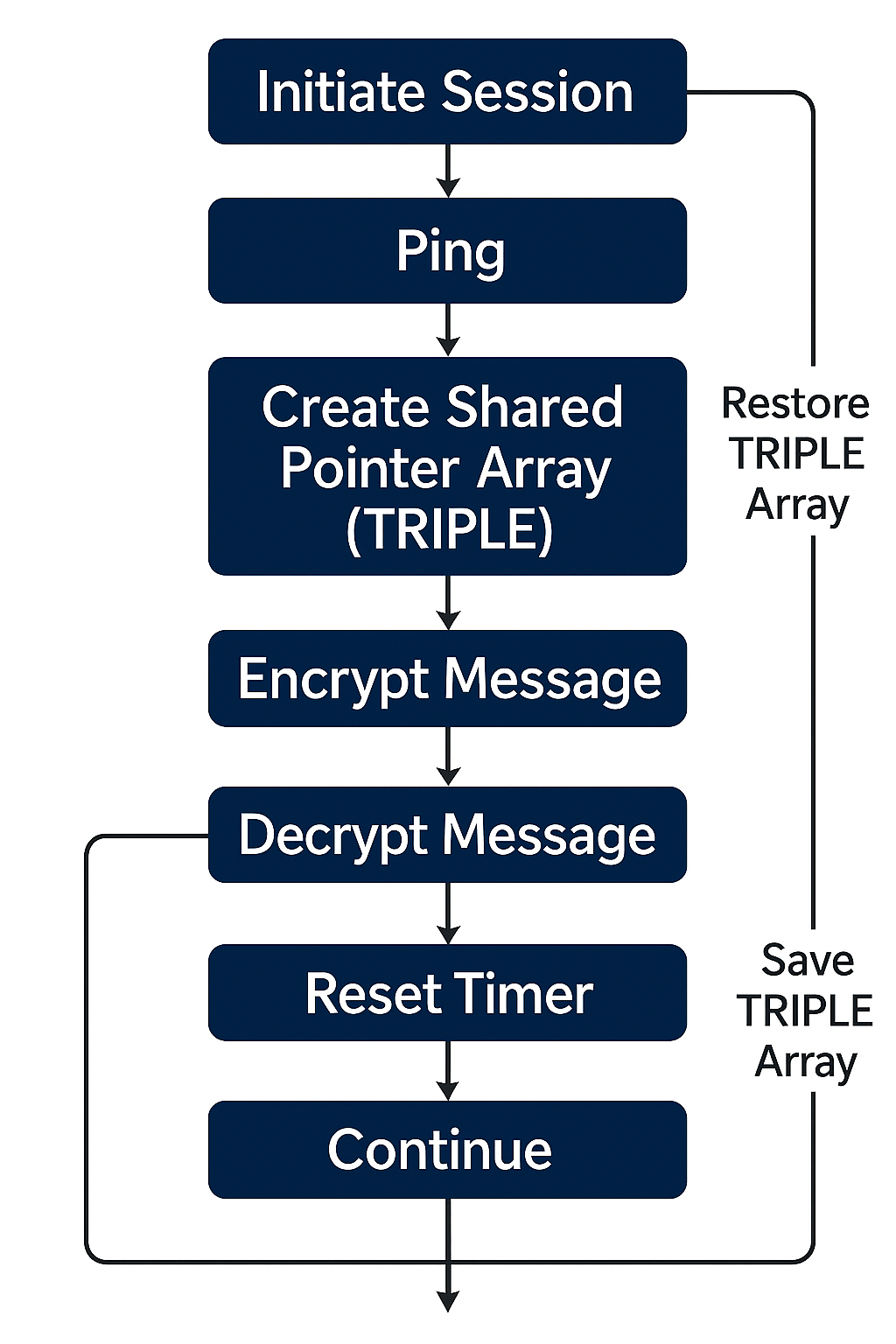
Protocol Overview
Complete communication flow from session initiation to secure message exchange and termination.
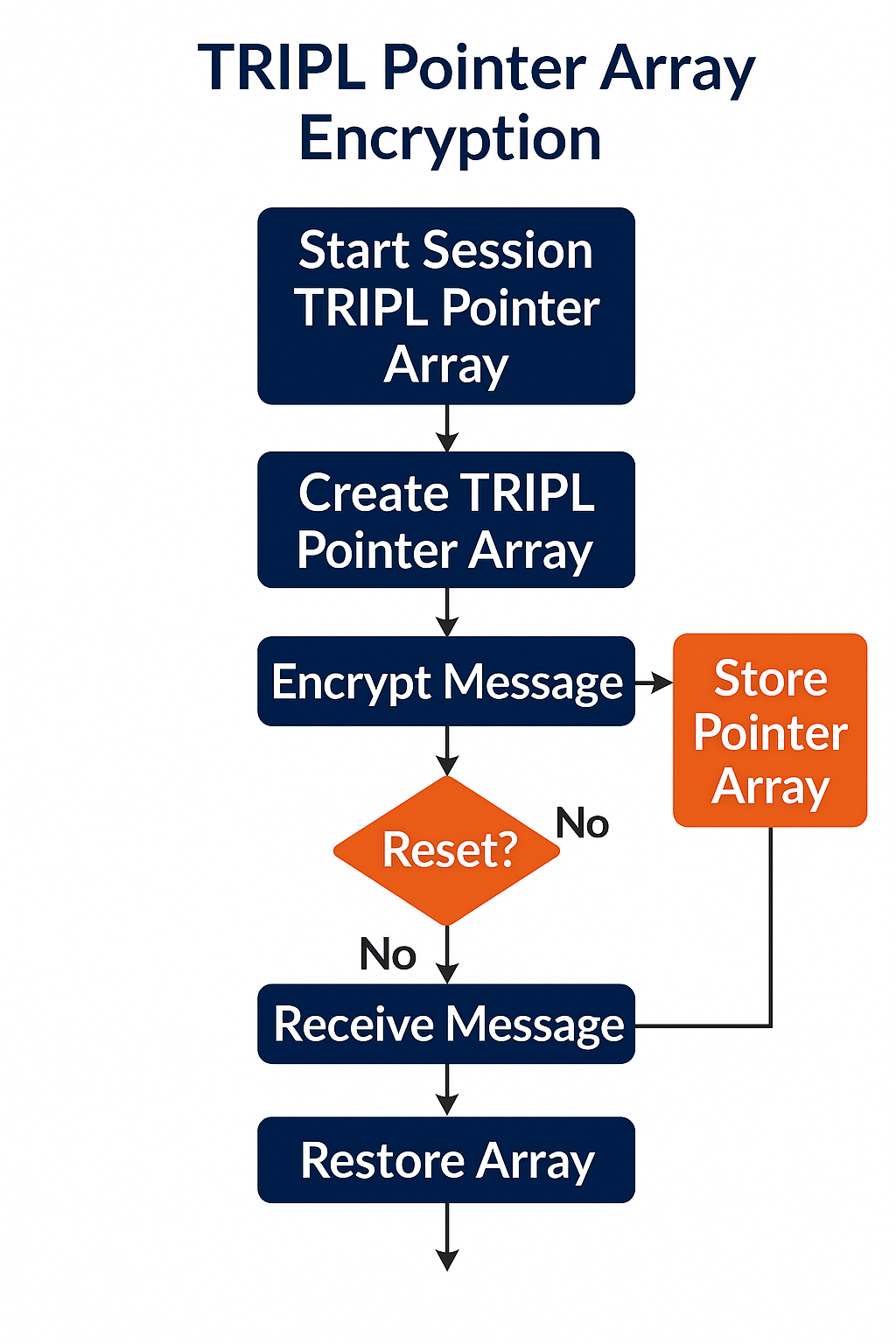
Pointer Array Encryption
Core encryption mechanism using polymorphic transformation and randomized pointer arrays.
Sender/Receiver Exchange
Bidirectional communication protocol ensuring synchronized encryption and decryption.
3. Technology Overview and Benefits
TRIPLE works by deriving encrypted values from pointer arrays linked to seed data. The encryption is polymorphic, context-specific, and continuously refreshed, resisting both mathematical analysis and key theft.
Core Technologies
Pointer-Array Logic
Uses memory pointers and array structures instead of mathematical algorithms for encryption transformations.
Polymorphic Transformation
Encryption method changes dynamically during each session, preventing pattern analysis.
Volatile Memory Processing
Encryption keys exist only in volatile memory and are never permanently stored.
Time-Based Resets
Encryption arrays reset automatically based on time intervals or traffic volume thresholds.
4. Technical Challenges and Implementation
TRIPLE mitigates key challenges through innovative solutions:
| Challenge | TRIPLE Solution |
|---|---|
| Pointer Synchronization | Shared seed data ensures identical pointer array generation |
| Reset Logic | Time-based and traffic-based triggers for array regeneration |
| Session Validation | Hashed session IDs prevent unauthorized access |
| Memory Security | Sandboxed Rust modules ensure secure memory handling |
| Reconnection | Pointer restore mechanism enables seamless session resumption |
5. Technical Documentation
Access comprehensive project documentation and technical prototypes for TRIPLE implementation:
Two pseudocode modules detail the TRIPLE_Main logic. One uses GeneratePointer(seed, index) for deterministic sessions. The other uses GetRandomPointer and ExchangeValue to dynamically co-generate session arrays between two devices.
6. Development Roadmap
The TRIPLE roadmap spans four critical phases from logic finalization to market deployment:
Logic Finalization
Complete core TRIPLE algorithms and pointer-array logic implementation with comprehensive testing.
Rust + WebAssembly
Build production-ready implementation using Rust for security and WebAssembly for cross-platform compatibility.
Session Recovery Validation
Validate dropped session recovery mechanisms and ensure seamless reconnection capabilities.
Browser Extension Deployment
Deploy TRIPLE in Chrome and Edge extension stores for widespread adoption and testing.
7. Red Zone Threat Analysis
TRIPLE anticipates current and future threats, including quantum decryption. Its polymorphic design, pointer resets, and lack of fixed decryption logic provide resilience even under surveillance or data theft.
Quantum Computing Resistance
Non-mathematical approach makes TRIPLE immune to quantum decryption algorithms like Shor's algorithm.
AI Interception Protection
Dynamic language generation prevents AI systems from learning communication patterns.
Memory Dump Security
Volatile memory processing ensures no persistent encryption keys survive system compromise.
Traffic Analysis Resistance
Polymorphic transformation prevents pattern recognition in network traffic analysis.
8. Unlike Regular Math-based Encryption
TRIPLE defies traditional encryption by not using math-based ciphers like RSA or AES. Critics might reject it as nonstandard, but that's its strength: it produces no decipherable pattern, no fixed key, and no algorithm to reverse.
Key Differentiators
| Traditional Encryption | TRIPLE Protocol |
|---|---|
| Mathematical algorithms (RSA, AES) | Pointer-array logic and memory structures |
| Fixed encryption keys | Dynamic, session-specific languages |
| Vulnerable to quantum computing | Quantum-resistant by design |
| Persistent key storage | Volatile memory only |
| Pattern-based encryption | Polymorphic transformation |
9. Conclusion
TRIPLE is fast, lightweight, and scalable. It aligns with zero-trust and minimal-resource strategies, offering encrypted messaging without heavy math or performance overhead. The protocol represents a fundamental shift in how we approach secure communications in an age of emerging quantum threats.
The following diagrams illustrate the TRIPLE protocol architecture:
TRIPLE creation, encrypted communication, pointer synchronization, and session resumption (see patent documentation for complete technical specifications).
Annex B â€" Signal Architecture & Language Analysis
Compares Signal's architecture (Java/Kotlin for Android, TypeScript for desktop, Rust for crypto) with TRIPLE's preferred stack. Recommends Kotlin, TypeScript, and Rust for similar platform compatibility.
Annex C â€" TRIPLE Web Browser Integration Strategy
Defines browser-based TRIPLE deployment using Chrome and Edge extensions. Details modes: HTTPS-bootstrapped and pointer-array resume via WebAssembly-compiled Rust.
Annex D â€" Signal Open-Source Code References
Lists open-source reference links: Signal-Android, Signal-Desktop, and libsignal for developers creating TRIPLE-compatible secure messengers.
Partner and Investor Opportunities
TRIPLE invites cloud providers, defense contractors, and secure communication platforms to partner, license, or invest in this next-generation platform.